Should I Be Concerned About the Safety of VPNs?
 Thanks to VPNs computer and hand-held gadget users can now browse the internet safely without having to worry about the possibility of hacking or the government interfering with their privacy. VPN service providers offer you both free and paid VPN services that you can easily access by a simple download click. If you are an Apple Mac owner, you can find online the 10 best VPNs for Mac that are offered by various VPN providers at affordable prices.
Thanks to VPNs computer and hand-held gadget users can now browse the internet safely without having to worry about the possibility of hacking or the government interfering with their privacy. VPN service providers offer you both free and paid VPN services that you can easily access by a simple download click. If you are an Apple Mac owner, you can find online the 10 best VPNs for Mac that are offered by various VPN providers at affordable prices.
While many appreciate VPNs have been able to protect their data online, not all users have confidence in its ability to protect their data. Choosing to use a VPN is a personal decision that is made with reasons only known to you.
However, in the recent past, after revelations of mass surveillance by governments, people have never been more concerned about their privacy. Technological companies were also not left behind as they sought to encrypt their data against potential surveillance and hackers.
Contents
ToggleSo, what is a Virtual Private Network?
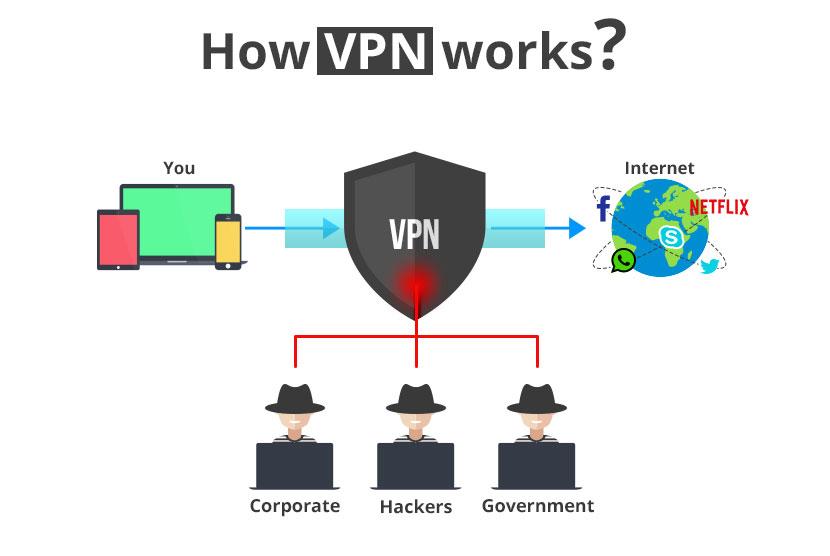
A Virtual private network is software that keeps your data private, encrypted and anonymous online. Your IP is masked. That means any other internet users interested with your data won’t get access to it even if they wanted to. For instance, when browsing using a public Wi-Fi, you could be accidentally disconnected. Even if disconnected, your data is still online. It could be hacked for malicious purposes or criminally-driven motives like someone trying to access your bank logs. However, a VPN makes you anonymous.
It routes your data online by giving you a new IP address that is different from your original IP address. It works by taking your data through a tunnel which only communicates between you and the web you are trying to access. There are no third parties involved and that means there are no privacy or security leaks that could expose you to hackers.
However, tunnelling in itself is not enough without a strong security protocol. VPNs have security protocols that also protect your data when you access networks with weak security. Pay attention to what types of VPNs you use as VPNs differ in their security protocols. Paid VPN services come with better security protocols than free VPNs.
Types of VPNs
Virtual Private Networks fall into two types:
Remote Access Virtual Private Networks
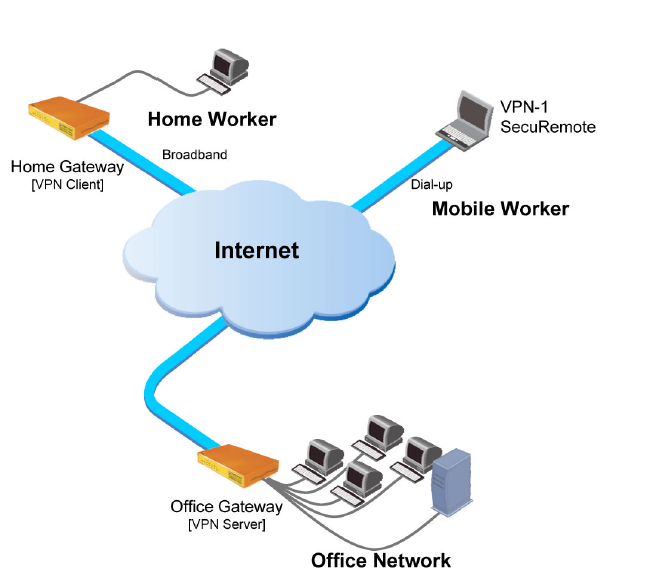
This type is commonly used by companies, businesses and home users. Users are able to access the internet through a private network that allows them to remotely use its services and resources. For instance, an employee away from the office can be able to access office files and materials in the office using a private network. Individual private users also use this type of VPN for their security and privacy.
Site to Site Virtual Private Networks
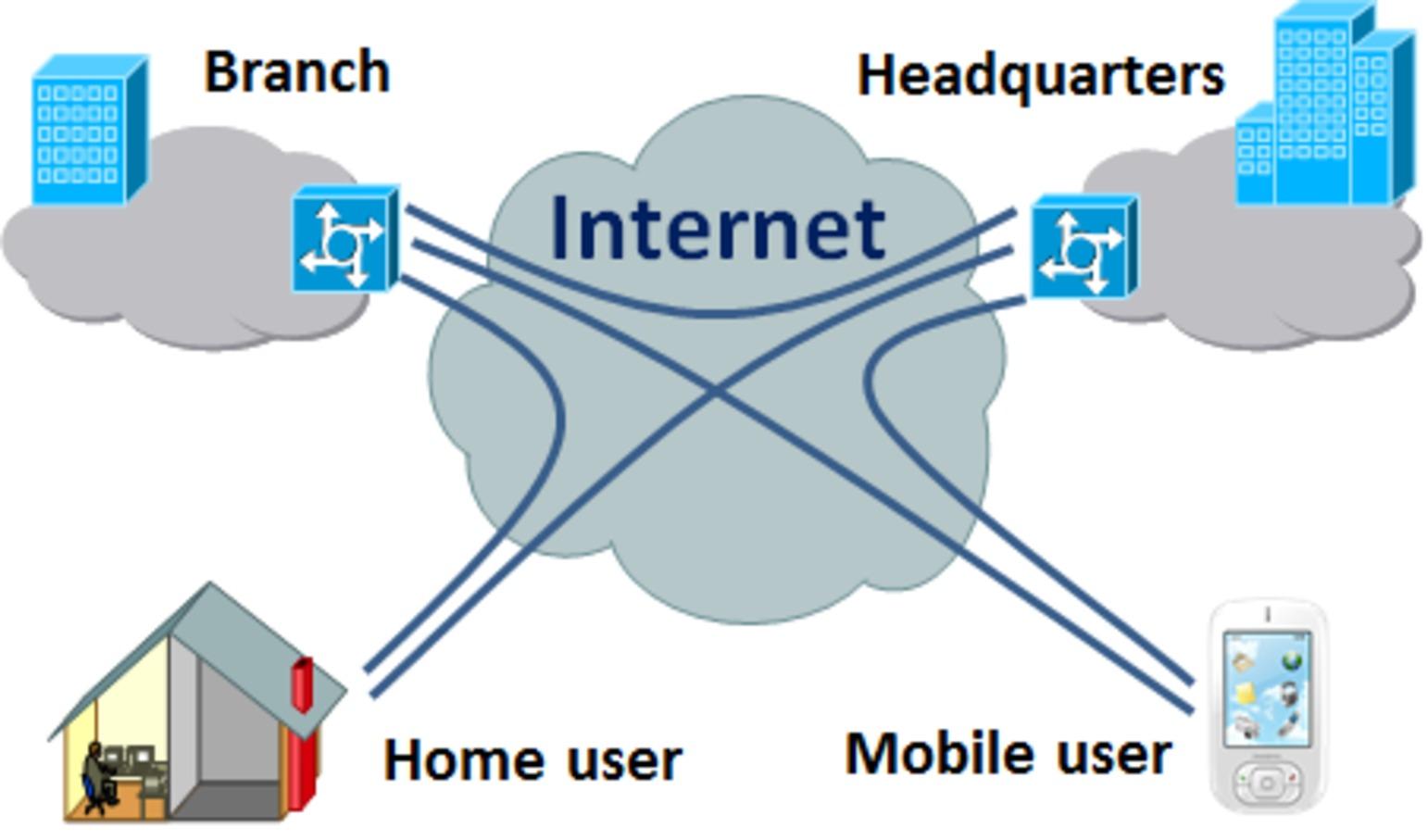
This type of VPN is used by large corporations or companies that have global operations in different geographical areas. To connect seamlessly and ease operations, they use this network, otherwise called a router to router VPN to connect the network of one office area to the network of another office location. The internet used by several office locations to connect their network turns out to be a VPN that is intranet based.
Site to site VPN can also be used by one company that wants to connect to the offices of another company. In this case, this VPN turns out to be Extranet based. A site to site VPN is ideal for creating a safe and secure network for companies that are in different locations geographically. Simply put, these companies are accessing the internet but through a private network that makes their communication private.
Could VPNs be a hoax?
In a bid to make private and protect their data against any kind of threats, many internet users have found solace in the use of VPNs to encrypt their data and make it anonymous. Even though they can’t verify that the VPN services they are using are 100% reliable, they are quick to admit they are keeping them safe. It is simply a benefit of doubt while telling yourself you are better off than the online user not having a VPN service.
Free VPNs

It is increasingly becoming difficult to know which the best VPN service in the market is. This is brought about by too many VPN companies in the market today. Many of them have similar features that make it confusing in knowing what VPNs suit your needs best. The question that not many are asking is whether this free VPN services everybody is rushing to are truly secure. In the past, free VPNs have been found to contain malware.
Paid VPNs

Paid VPNs are no exception as well. VPN developers could simply breach user trust and leak their private data to third parties without their knowledge. Methinks if the trust and confidentiality of VPNs cannot be verified, then you do yourself a great favor by staying away.
Risks that come with a VPN
Yes, it is a post-Snowden era and everybody is now aware of mass surveillance. However, Snowden revelations and the information it leaked only gave little power to citizens and not absolute power. Your government can still access your bedroom, living room and digital data at will. Here are some risks that come with the use of VPNs:
- Could be fake and come with malware
- VPNs trading with your browsing data
- VPNs services that log your data
- VPNs with heavy encryption reduce your browsing speed.
Final thoughts
Keeping safe is the primary responsibility of every sane person. In the 21st century, keeping safe has also to do with your digital data. A Virtual Private Network gives you the benefit of browsing online incognito. Your data is encrypted and taken through a VPN tunnel that also encrypts it more. This makes it hard for hackers to trace you online. However, many VPN users cannot verify its reliability to keep your data protected as it claims. Use a VPN if you want to but don’t have absolute trust in its ability to protect you. It could turn out to be your worst enemy.
Recommended For You
What Are The Prerequisites To Learn Artificial Intelligence
Most Inside
Most Inside offers high-quality recommendations and valuable updates to enhance all aspects of your life, providing premium guidance and enriching experiences.





Every software developer has to acquire funds somewhere, and if you have no real idea where your VPN provider gets the money from, you might be in danger. I’m not a fan of paying big money for open and safe internet, and I’m not happy my ISP can’t assure that either, so, I’ve been looking for a good VPN deal this Black Friday. I checked the ratings on vpnranks regarding the price, and Surfshark came first, going for just 1.99$/month for a two-year plan using “BLACKSHARK” coupon. I think it’s affordable and there’s no need to worry about the risks of free VPN.